Why AES is so secure?
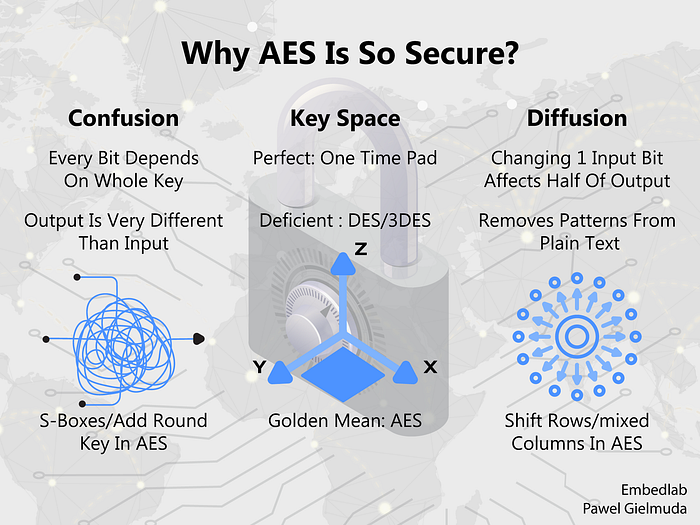
That’s a valid question since this standard is so popular. Firstly let’s look at the key space and compare the time of cracking it by brute force method (by checking every possible key).
- For One Time Pad cipher, key length is equal to the length of plain text i.e. for 100 characters of plain text this would mean a 2⁸⁰⁰ key combination which is uncrackable.
- For the predecessor of AES- DES algorithm this is 2⁵⁶ (7-character password) and from 2012 this could be broken in less than 24h
- For AES the lowest key length is 128 (16-character password) and currently it would take one billion years to crack that.
Please notice how small the difference in key length (7 vs 16 character password) means very big difference in security.
But brute force is not a smart algorithm. To be robust to more sophisticated types of attacks AES needs to have two properties: confusion and diffusion.
Confusion means that a single output bit depends on every bit of the key. This would mean that the ciphertext will not give any clue about the plain text. Substitution (S-Box) round combined with XORing output with round key ensures that characteristic.
Diffusion is quite different. It’s not related to the key. Its main goal is to remove any patterns from the plain text and harden to the so-called frequency analysis of the cipher text. This is realized by mixing columns and shifting rows in AES.
As you can see the design of the AES standard is not just a brilliant guess but is more a result of understanding how the cipher could be attacked and how to deal with that. But the types of attacks are a different story.